To improve the skills of students majoring in cybersecurity, the university has a virtual laboratory called the cyber range. Using the cyber range, students can implement network attacks and repel them, identify software vulnerabilities, restore the affected infrastructure and investigate the effectiveness of mechanisms for preventing and recovering from attacks, the peculiarities of the malware life cycle, and much more.
The central concept of the Cyber training ground virtual laboratory is safety and safety again!
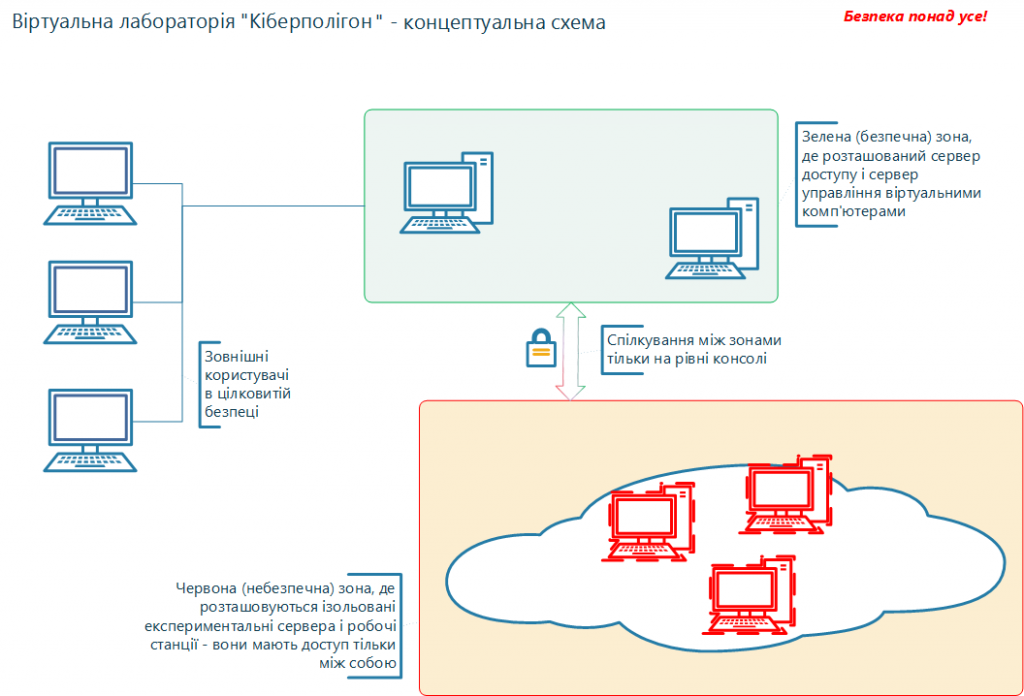
Fundamental measures that create a safe environment for learning about aggressive software environments and applications:
- dividing the zones of the virtual laboratory into sectors: green - safe, red - dangerous, where hazardous work will be performed;
- complete physical isolation between environments;
- external users work with “toxic” environments only through the console - no direct contact;
- virtual servers and workstations running the software under investigation are connected by an isolated switch - no external access;
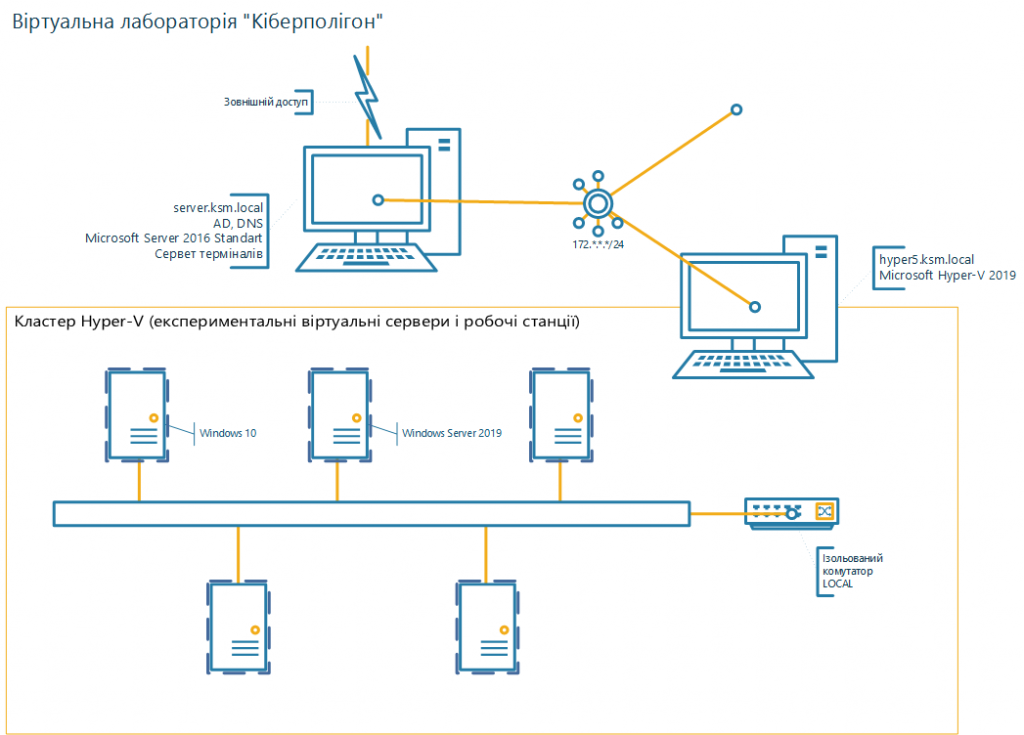
To ensure the fulfilment of the tasks assigned to the laboratory, the following main components are provided:
- pre-deployed and configured virtual machines
- capabilities for archiving virtual machines at any stage of research
- full administrative rights for researchers at research sites
- productive server hardware that supports virtual machines
- redundancy of the system as a whole
Due to the simplicity of changing and configuring virtual machines, the cyber range's architecture allows researchers to focus on the tasks at hand and perform work from the university and with access to external networks.