On October 29 at 1:00 p.m., a lecture was held at Khmelnytsky National University with the participation of Oleksiy Fedorov, Head of the Department of Digital Development, Digital Transformation, and Digitalization of the Khmelnytsky Regional State Administration, as well as faculty and students of the Department of Cybersecurity. The lecture was devoted to issues related to the implementation of Law No. 4336-IX.

Law of Ukraine No. 4336-IX "On Amendments to Certain Laws of Ukraine Regarding Information Protection and Cyber Protection of State Information Resources and Critical Information Infrastructure" is a fundamental reform in the field of national cybersecurity. Its adoption was prompted by the unprecedented growth of cyber threats, which have turned cyberspace into a field of active combat, and Ukraine's strategic course towards European integration, which requires harmonization of legislation with EU standards, in particular with the ISO/IEC 270xx and ISO/IEC 15408 series standards, the international frameworks NIST and ENISA, the GDPR regulation, etc.
Key changes include the creation of a multi-level National Cyber Incident Response System, the introduction of a unified platform for sharing information about cyber threats, and the establishment of mechanisms for proactive vulnerability detection. The law introduces mandatory staff positions for cyber security managers and specialists in government agencies and critical infrastructure facilities, as well as regular cyber hygiene training for all employees.
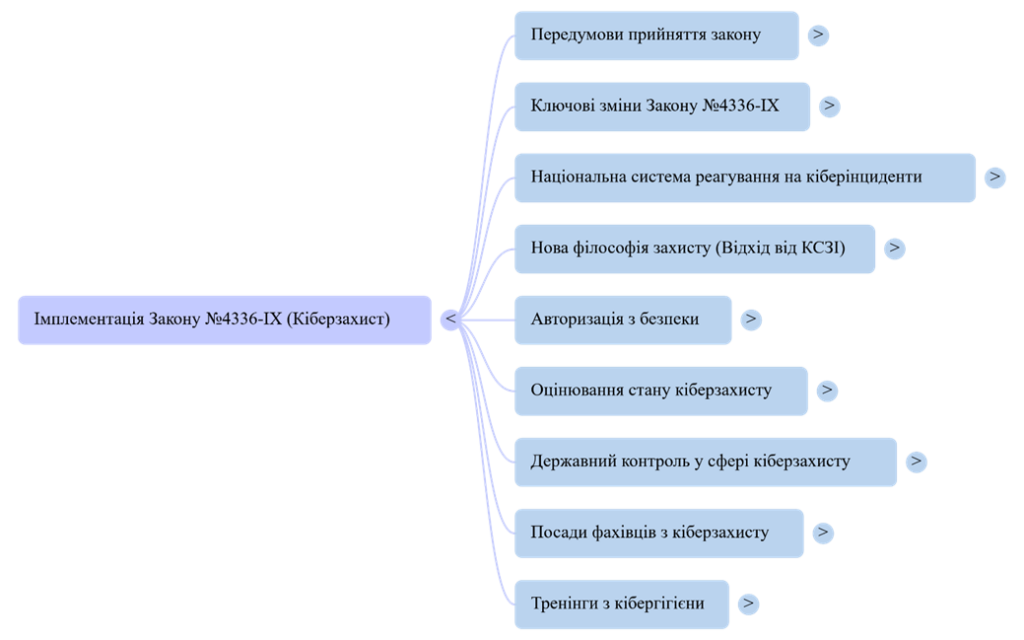
One of the most significant transformations is the strategic shift away from the outdated model of the Comprehensive Information Protection System (CIPS), which has compromised itself, to a new protection philosophy based on international practices – system authorization for security. This approach is more flexible and effective, based on cyber risk management, development, and regular assessment of security profiles.
To implement the law, a number of regulatory acts have been developed and adopted to regulate the processes of authorization, assessment of cyber security status, and state control, which will be carried out through monitoring, scheduled and unscheduled inspections.
The speaker shared his own experience in system security authorization, emphasizing current and problematic aspects.
Teachers and students took an active part in the discussion of the basic provisions of the law and the prospects for its implementation.
The participants of the event express their sincere gratitude to Alexey Fedorov for his interesting presentation and the opportunity to learn from the relevant experience of a professional practitioner.


