Connecting to an electronic information network has become an integral part of our daily life. All kinds of organizations such as medical, financial and educational institutions use this network to function effectively. They use the network to collect, process, store and share large amounts of digital information. The more digital information is collected and the more often it is shared, the more important it becomes to protect that information.
Cybersecurity is an ongoing effort to protect network systems and all types of data from unauthorized use or damage. On a personal level, you need to protect your account, data and electronic devices. At the corporate level, the responsibility of each employee is to protect the reputation of the organization, its data and customers. At the state level, it is a matter of national security, as well as the safety and well-being of citizens.
The more time you spend online, the more your life can be affected by your identity both online and offline. Your offline identity is yourself, the person your friends and family interact with every day at home, school, or work. People around you know your personal data, namely your name, age or place of residence. Your online identity is who you are in cyberspace. Your online identity is how you present yourself to others online. This online identity should only reveal a minimum of information about you.
Be careful when choosing a username or nickname for yourself online. The username must not contain any personal information. It should be something appropriate and acceptable. Your username should not lead others to think that you are an easy target for cybercriminals or want to attract unwanted attention.
Any information about you may be considered your personal data. This personal information can uniquely identify you as an individual. This data includes photos and messages you share with family and friends online. Other information, such as name, date and place of birth or mother's maiden name, is known only to you and is used to establish your identity. Information such as medical, educational, financial, and employment information may also be used to identify you online.
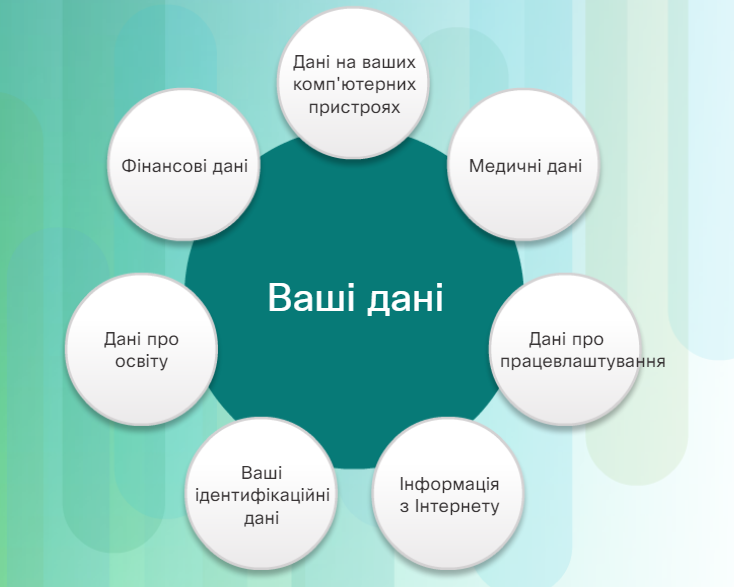
Your computing devices don't just store your data. Now these devices have become a portal for your data and generate information about you.
Unless you choose to keep all personal information on paper, you use your computing devices to access the data. If you want a digital copy of your most recent credit card statement, you use your computing devices to access your credit card issuer's website. When you want to pay your credit card bill online, you access your bank's website to transfer funds using your computer devices. In addition to allowing you to access your information, computing devices can also generate information about you.
With information about you available online, your personal data can become useful for hackers.
Your network credentials are valuable. They give attackers access to your accounts. Criminals can also use information about your family relationships. They can access your online accounts to get you to transfer money to your friends or relatives. A criminal may send a message saying that your family or friends need your help in the form of a money transfer to return home from abroad after losing their wallets.
Criminals are very sophisticated when they try to get you to hand over money. They don't just steal your money. They can also steal your identity and ruin your life.
It's not enough for criminals to steal your money for short-term monetary gain, they want long-term profit by stealing your identity.
Using a stolen identity, they can open credit accounts and accumulate debt in your name. This will hurt your credit score and make it harder to get loans.
Personal credentials can also provide access to corporate data and state secrets.
Source: